Module 4 - Basic Digital Security
Introduction
Now that you’ve learned about the right to privacy, as well as the basics of data protection, it’s time to learn about one of the most practical ways to protect the privacy of your personal and organizational data: digital security. Digital security is a broad topic and one that constantly changes due to the nature of digital technologies. Therefore, instead of focusing on the technical skills and tools, this module aims to equip learners with the correct mindset on security, the basic risk assessment framework, and free and open-source tools they may use in their everyday lives.
Having a sound digital security framework begins with knowing what security is, and what it isn’t. An integral part of this is debunking common misconceptions about what digital security entails.
Common security myths
The goal is to achieve 100% perfect security. – NOT TRUE. There is no such thing as perfect security. Digital security is a continuous and never-ending process, and not a single outcome that can be achieved with one training.
The strength of an organization’s digital security relies on how sophisticated are the tools that they use – NOT TRUE. Sometimes tools even make it more difficult. There is no point in using lots of tools if you are not doing basic security measures such as using virus scans, encrypting your device, good password management, etc.
There should be one person that is concerned with the digital security of an organization – NOT TRUE. Security (physical or digital) is an organizational effort. It only takes one weak link to corrupt the whole chain, so digital security knowledge and capacity should be distributed among all members of the organization. Security is like vaccinations. It only works when everyone is using it.
Digital security tools are expensive – NOT TRUE. Free/Libre Open Source Software (FLOSS) are readily available and are recommended by digital security experts. This means that the users have the freedom to run, copy, distribute, study, change and improve the software. Therefore, security experts are able to freely examine the software for any bugs or vulnerabilities, allowing the community to properly vet the security of the tool.
Definition of security
Security is the process of protecting an asset from any danger or threat.
Risk assessment/analysis
Risk analysis is the process of calculating the chance that threats might succeed, so you know how much effort to spend defending against them. Assessing risks means deciding which threats you are going to take seriously, and which may be too rare or too harmless (or too difficult to combat) to worry about. Basic risk assessment involves asking yourself (or your organization the following questions:
What do I want to protect? (asset)
What do I want to protect it from? (threat)
Who do I want to protect it from? (adversary)
How bad are the consequences if I fail? (impact)
How likely is it that I will need to protect it? (likelihood)
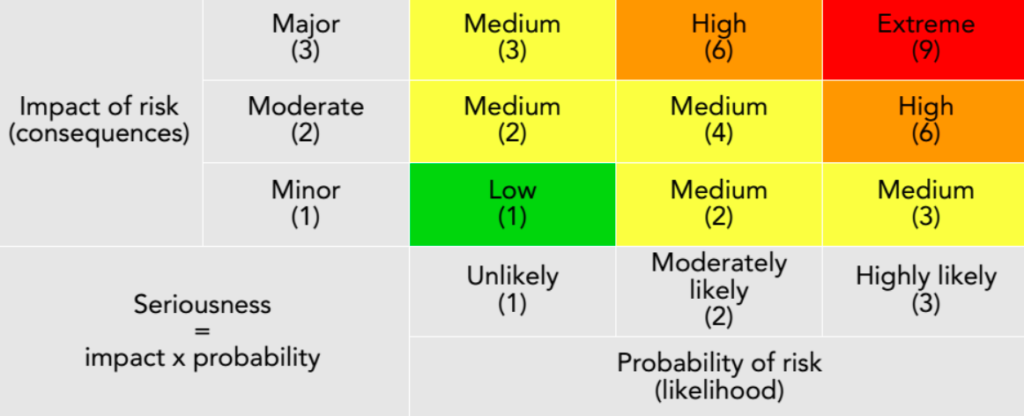
Risk = Impact x Likelihood
The risk level (from 3f) should then be located in the matrix below to identify priority level. This will then help you or your organization develop a security plan, starting from the specific risks that you’ve identified as high-priority from the risk assessment exercise.
Key points for digital security
One does not need to be technologically adept to be able to protect their privacy and security online. Digital security starts with being diligent about the security measures that we do on a regular basis, such as creating/changing passwords and creating online accounts. Below are some easy and practical tips to make your online presence more secure:
Have a strong password
The longer the password, the better. This makes it more difficult for both human adversaries and automated bots to crack your password.
Complexity – As with length, using a variety of characters also makes a password more difficult to crack. Here are some tips to make your passwords complex but easy to remember:
Varying capitalization (e.g., iAmYouRmoThEr)
Alternating numbers and letters (e.g., s3cuR1ty)
Incorporating certain symbols (e.g., mYb0dy#MyRuL3s)
Use traditional mnemonic devices such as acronyms. This allows long phrases to be turned into complex, seemingly random words. (e.g., “To be or not to be? That is the question” becomes 2Bon2B?TitQ)
Regularly change your passwords, particularly for your most sensitive accounts.
Use a passphrase or several words put together.
Use a password manager such as KeepPass. This will not only help you generate secure passwords, but will also help you avoid the problem of forgetting your passwords, as you will only need to remember one master password for all your accounts.
Use two-factor (or multi-factor authentication)
2FA or MFA is an extra layer of security that requires not just a password or username but also something else that ONLY the user has on them. Some examples of 2FA are PIN, token key, cell phone number, fingerprint, or voice.
Use secure means of communication (end-to-end encryption)
Encryption is a protocol by which the message will be scrambled and unreadable by anyone except the intended recipient. Most instant messaging apps nowadays such as Viber, Telegram, and even Facebook Messenger claim to have end-to-end encryption features. However, security experts still recommend FLOSS messaging applications. Some examples of open-source encryption tools are provided below:
Instant messaging: Signal, Wire
Email: Riseup, Protonmail
Practice anonymous browsing
Use a VPN, when possible
A VPN or virtual private network, masks your location when browsing the web by making it seem that all the data that you send is originating from the VPN location rather than your own internet service provider. This masks your IP address (a unique identifier for your device), therefore adding a layer of anonymity and privacy in your browsing. There are many VPNs available to be used, and this guide might help you choose what’s best for your particular need.
Alternative search engines
Unlike most popular commercial search engines, alternative search engines like DuckDuckGo pays particular attention to privacy controls and protection, including features such as tracker blockers and encrypted connections. DuckDuckGo also doesn’t track one’s search history. Meanwhile, apart from blocking trackers, the Tor Browser uses “onion routing,” or the practice of using multiple layers of encryption to better anonymize the identities and locations of parties using the network.
Browser extensions
Even while using commercial browsers such as Google Chrome, one can still practice some level of privacy by using browser extensions like Privacy Badger, which automatically blocks invisible trackers and sends companies signals to opt you out of tracking and data sharing and selling.
Keep regular back-ups
Regularly keep track of where your data is stored and how often that data should be backed up. This mitigates the risks associated with losing your access to any of your devices or accounts. The frequency of backups may also depend of the level of sensitivity of the data involved (thus, the need for a risk assessment).
Always ask the following questions:
Why type of information am I storing?
How important is this information?
How often is it produced or changed?
How often must it be backed up?
Use open-source alternatives
Collaborative documents (alternatives to Google Docs): Cryptpad, Etherpad
Search engine (alternatives to Google Chrome): DuckDuckGo, TOR
Digital security at the time of the pandemic
When the COVID-19 pandemic broke out in 2020, individuals and organizations alike became dependent on digital technologies for tasks that used to be accomplished offline. As the world shifts closer to a digitized society, new security threats also emerge, and more people are exposed to them. As we transition into becoming “digital citizens,” below are some practical tips and reminders by which we can protect our privacy and the security of our data and devices.
Contact tracing tools
With the lack of a single, functional and unified contact tracing tool in the country, most people are forced to download and install a multitude of contact tracing applications on their devices. However, each of these applications also come with their own privacy and security risks, as they all collect and process sensitive personal information. Some contact tracing applications have also reported data breaches. How can we protect our data from such threats?
Check if they’re official – Local government units would usually have an ordinance that declares which contact tracing tools are for official use. It would be useful to check these before installing to avoid giving out your data to unofficial apps that pretend to be authorized just to collect your personal data.
Check if they’re voluntary – Not all contact tracing apps are mandatory. If you are given a choice, it is safer to install as few contact tracing apps as possible.
Check permissions- Some applications also give users some level of control as to the kind of data they collect. This is usually done during the process of installing the app. Check if there are any app permissions that you can opt out of.
Remote learning
Teach kids basic digital security and etiquette – With classes moving online, kids are forced to become digital citizens earlier than before. It is therefore crucial to teach children not just the skills needed to navigate the digital world, but also those they need to stay safe and secure on the internet.
Only install software that are vetted and/or required by the school – The transition to online/remote learning necessitates the use of various learning and communication platforms. However, parents should be mindful of what tools or platforms are used by the school, and what can be deleted or disposed of. This minimizes the risks and threats that kids are exposed to.
Remote work
Conduct regular security checks – With employees now working in different locations, with different kinds of internet connection and levels of security in their homes, it is more important than ever to ensure that all members of the organization are on the same page when it comes to security practices. Employers must ensure that there is at least a standard baseline understanding of security policies, practices, and protocols among ALL members of the organization.
Draft a security policy for office-issued devices – Considering that many employees are using office-issued devices at home, the employer must set a policy for the use and upkeep of such devices.
Practice regular backups – This should be standard practice in organizations even outside the context of remote work. Keeping regular backups minimizes the impact of possible cases of loss of devices or unauthorized access to official accounts.
Where to seek help
Philippine National Police Anti-Cybercrime Group
Complaint Action Center Hotline: +63 961 829 8083 (Smart) and +63 9155898506 (Globe)
Facebook: https://facebook.com/anticybercrimegroup
Twitter: https://twitter.com/pnpacg
National Privacy Commission
Email: complaints@privacy.gov.ph
NPC Trunk line No: 8234-2228
Local numbers:
For registration & compliance concerns– 118
For complaints– 114
For other inquiries– 117
Department of Justice Office of Cybercrime
Email: cybercrime@doj.gov.ph
Telephone number: 526-2747 / 521-8345
Other information: https://www.doj.gov.ph/reporting_cybercrime.html
Foundation for Media Alternatives
Although FMA is not a direct-service organization, we may be able to refer you to other civil society organizations or government agencies, or provide you with resources that could address your concern.
AccessNow Digital Security Helpline
Website: https://www.accessnow.org/help
Email: help@accessnow.org
Digital Security Resources:
Digital First Aid Kit https://digitalfirstaid.org/en/
Organisational Strength Map https://ifex.org/toolkits/organisational-toolkit/organisational-strength-map/digital-security/
Umbrella security handbook mobile app https://secfirst.org/umbrella/
Security in a Box https://securityinabox.org/en/
Safe and Documented for Activism: Security Policies and Procedures for Activist Organisations https://sdamanual.org
Digital Security for All http://www.digitalsecurityforall.com/en
Surveillance Self-Defense: Tips, Tools and How-Tos for Safer Online Communications https://ssd.eff.org/en/module/your-security-plan
Digital Security Tools:
KeePassXC (password manager): https://keepassxc.org/
Protonmail (encrypted email): https://proton.me/
ProtonVPN (VPN): https://protonvpn.com/
DuckDuckGo (alternative search engine): https://duckduckgo.com/
Secure messaging apps:
Signal: https://signal.org/en/
Wire: https://wire.com/en/
Collaborative document editor (alternatives to Google docs)
Etherpad: https://etherpad.org/
CryptPad: https://cryptpad.fr/